MikroTik Conversion Guide
Prerequisites
- RouterOS v7 device running CAPsMAN 2 (tested on 7.18.1)
- RadSecProxy container running in your network.
- For self-serve, CLI wallet prepared for onboarding: https://docs.helium.com/mobile/helium-plus-onboarding/
- For Helium Plus, certificates (
ca.pem,cert.pem,key.pem) supplied by the Helium Plus team and copied into the RadSecProxy directory. - UDP ports 1812/1813 open between MikroTik and the RadSecProxy host.
- Bridge interface already created and used as the datapath for Wi-Fi traffic.
High-Level Steps
- Deploy the RadSecProxy container and note its IP.
- Create a RADIUS profile that points to the RadSecProxy.
- Build a Wi-Fi configuration profile for the Helium Passpoint SSID.
- Apply the profile to an interface (or create a virtual AP).
- Verify operation and troubleshoot, if necessary.
1. Deploy RadSecProxy
At time of writing, RouterOS does not support RadSec natively, download the RadSecProxy container and run it in a Docker.
- Un-zip and untar the
Helium_RadSec_Docker.tar.gzfile into the directory of your choice on the host machine. This will unpack the following items:Dockerfile- The docker instructions on how to build the containerRadsecproxy.conf- The radsecproxy config file is pre-populated to connect to Helium Network AAA serversdocker-compose.yml- File to start and stop the container as a daemon.
tar -xvzf Helium_RadSec_Docker.tar.gz
- Into the same directory copy the 3 certificates obtained from Helium Network
ca.pem- the root CA certificatecert.pem- the user certificatekey.pem- the key file matched to the certificate
- Start the container using:
sudo docker compose up -d
- If/when needed, stop the container using:
sudo docker compose down
Once the container is running, make sure you can ping it from the MikroTik router.
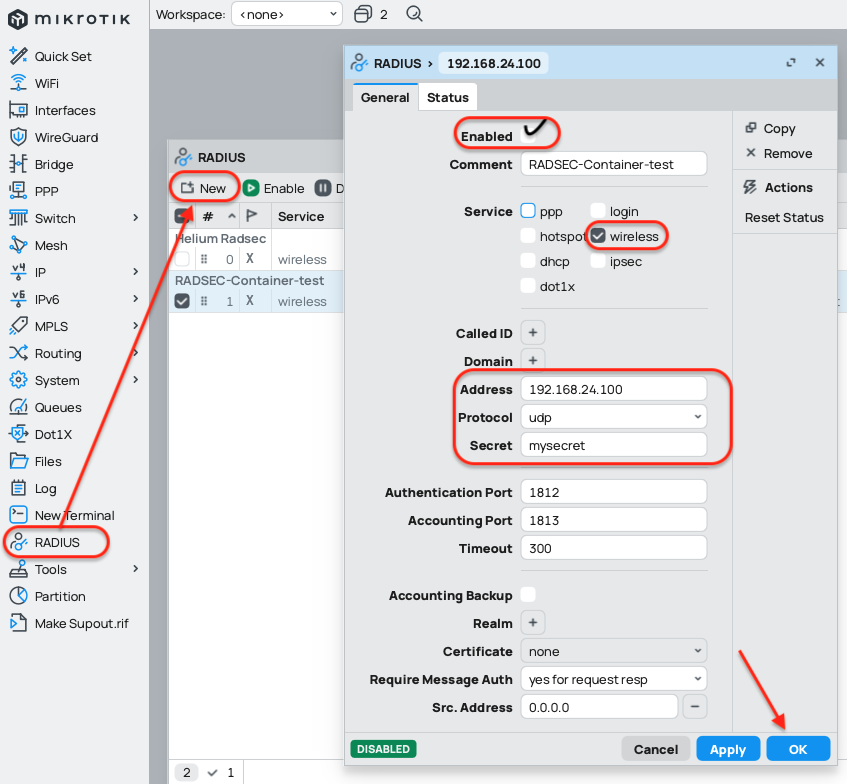
2. Add a RADIUS Profile
In RADIUS add a new entry:
| Field | Value |
|---|---|
| Comment | Helium AAA |
| Service | wireless |
| Address | IP_of_RadSecProxy |
| Protocol | udp |
| Secret | mysecret |
| Authentication Port | 1812 (default) |
| Accounting Port | 1813 (default) |
| Timeout | 300 s |
| Enabled | ☑︎ |
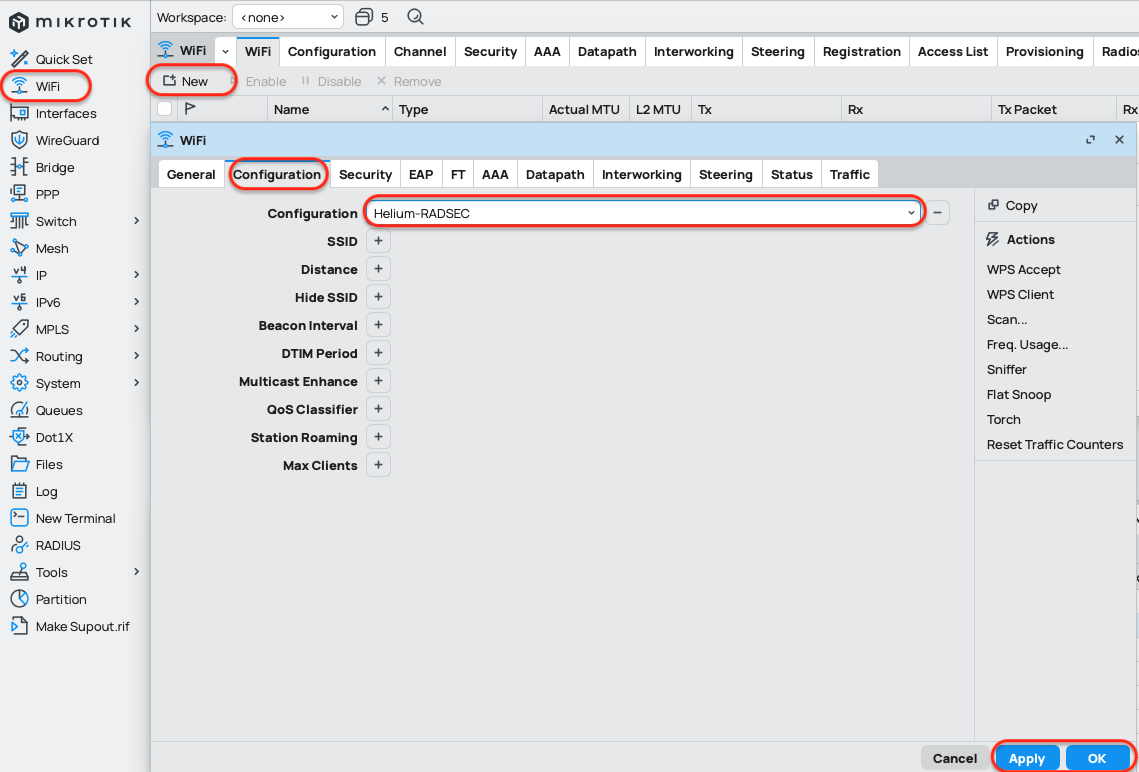
3. Create a AP Configuration Profile
Navigate to WiFi → Configuration and click Add (+).
Configuration Tab
| Field | Value |
|---|---|
| Name | helium-passpoint |
| Enabled | ☑︎ |
| Mode | ap |
| SSID | Helium |
Channel Tab
Select the band and channel width appropriate for your deployment. Leave Frequency blank for automatic channel selection.
Security Tab
Check WPA2 or WPA3 EAP under Authentication Types.
EAP Tab
Check EAP Accounting to be enabled.
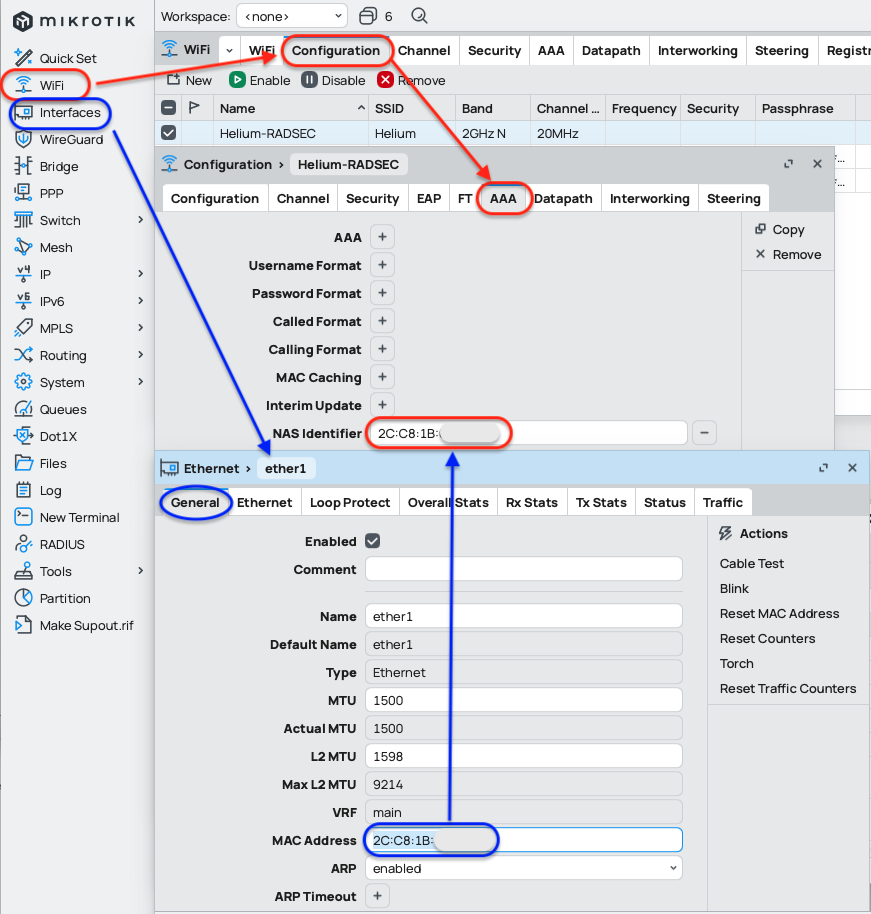
AAA Tab
Paste a MAC address of the WAN interface (usually ether1 by default) from menu Interfaces. Or enter the NAS-ID provided during Helium Plus onboarding.
Datapath Tab
| Setting | Value |
|---|---|
| Bridge | bridge1 (or the bridge used for LAN) |
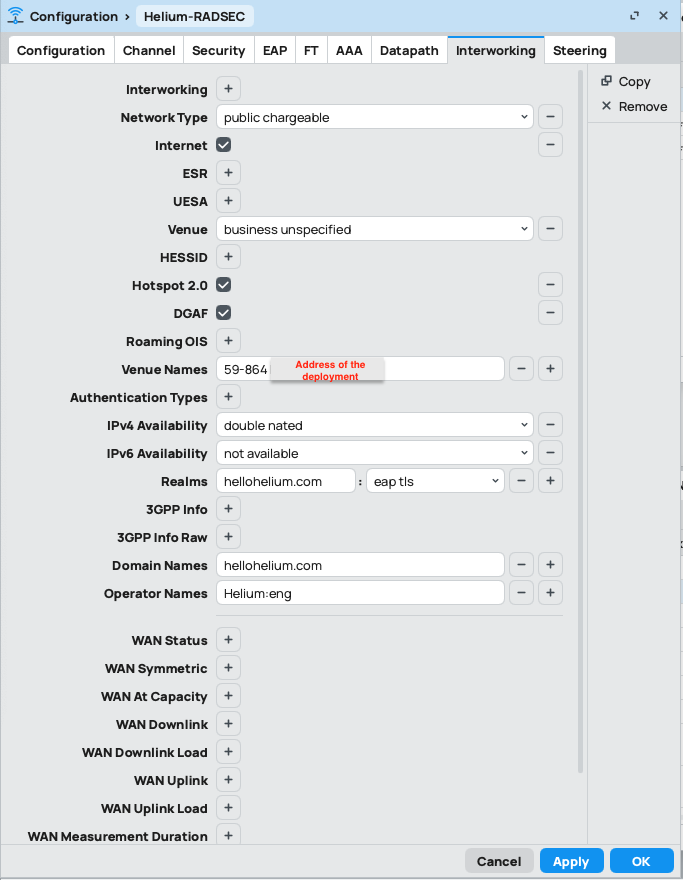
Interworking Tab
Fill in as shown:
4. Attach the Profile to an Interface
Assign the configuration profile to the desired WiFi interface. Either click New (this will create a virtual AP) or Edit an existing master interface.
Make sure to select a correct 5/2.4 interface according to the band defined in the configuration profile.
Enable it on the General tab.
5. Verification
- Confirm that the
HeliumSSID is visible. - In logs, watch for successful
radiusauthentication messages. - On the RadSecProxy host use
docker logs -f radsecproxyto ensure TCP/TLS sessions are established. - On a compatible handset, ensure automatic connection with the carrier profile.